This article provides step-by-step instructions for deploying imper.ai with Google Workspace.
The deployment enables imper.ai to integrate with Google Workspace as an Identity Provider (IdP) and to protect Google Meet sessions using identity-aware verification.
The process includes:
Connecting Google Workspace as an IdP in imper.ai
Configuring Domain-Wide Delegation in the Google Admin Console
Authorizing required Google API permissions
Completing Google Workspace onboarding in imper.ai
Follow the steps in the order listed. This article assumes that all prerequisites have been met and that the deployment sequence has been reviewed.
Prerequisites
Before you begin, ensure that:
You have Google Workspace Super Admin privileges
You have Admin access to the imper.ai Admin Console
Google Workspace is selected as your Identity Provider (IdP)
You have access to the imper.ai App (Client) ID provided during onboarding
Deployment Procedure
Step 1: Connect Google Identity Provider (IdP)
Log in to the imper.ai Admin Console using administrator credentials or SSO.
Navigate to Settings > Integrations.
Locate Google Workspace and click Connect. The Google Integration pop-up opens.
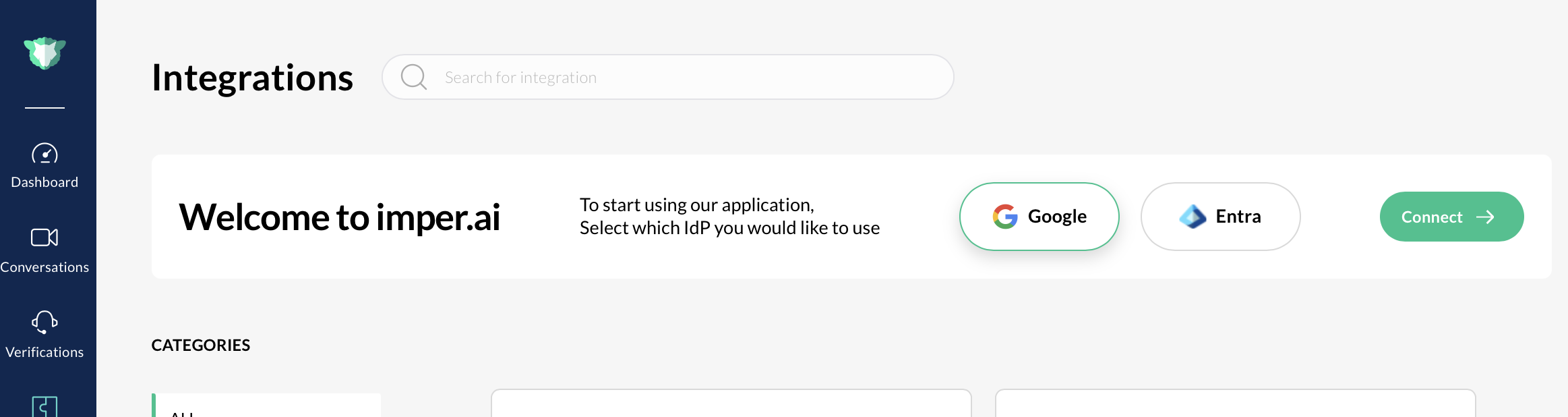
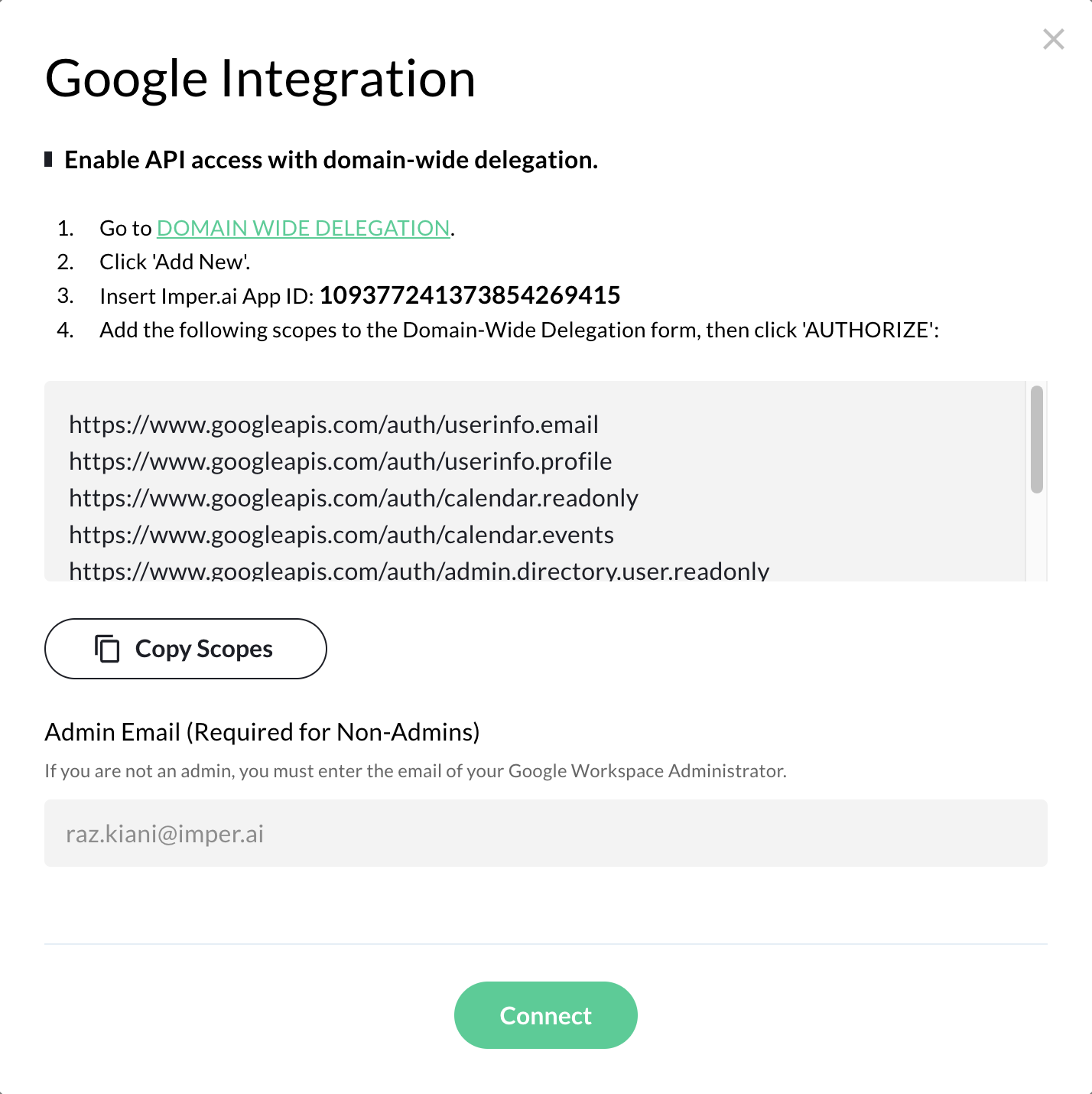
Note: If the user logging in to the Imper.ai console is not an administrator, you must provide the “Admin Email (Required for Non-Admins)” field and enter the email address of your Google Workspace Administrator.
Step 2: Copy Scopes from imper.ai
In the Google Integration pop-up window, click Copy Scopes.
Keep the scopes copied. You will paste them into the Google Admin Console in a later step.
These scopes define the Google APIs imper.ai is authorized to access.
Step 3: Open the Google Admin Console
You can access the Google Admin Console in one of the following ways:
Click the Domain-Wide Delegation link directly from the imper.ai integration pop-up
OR
Manually sign in to the Google Admin Console using a Super Admin account
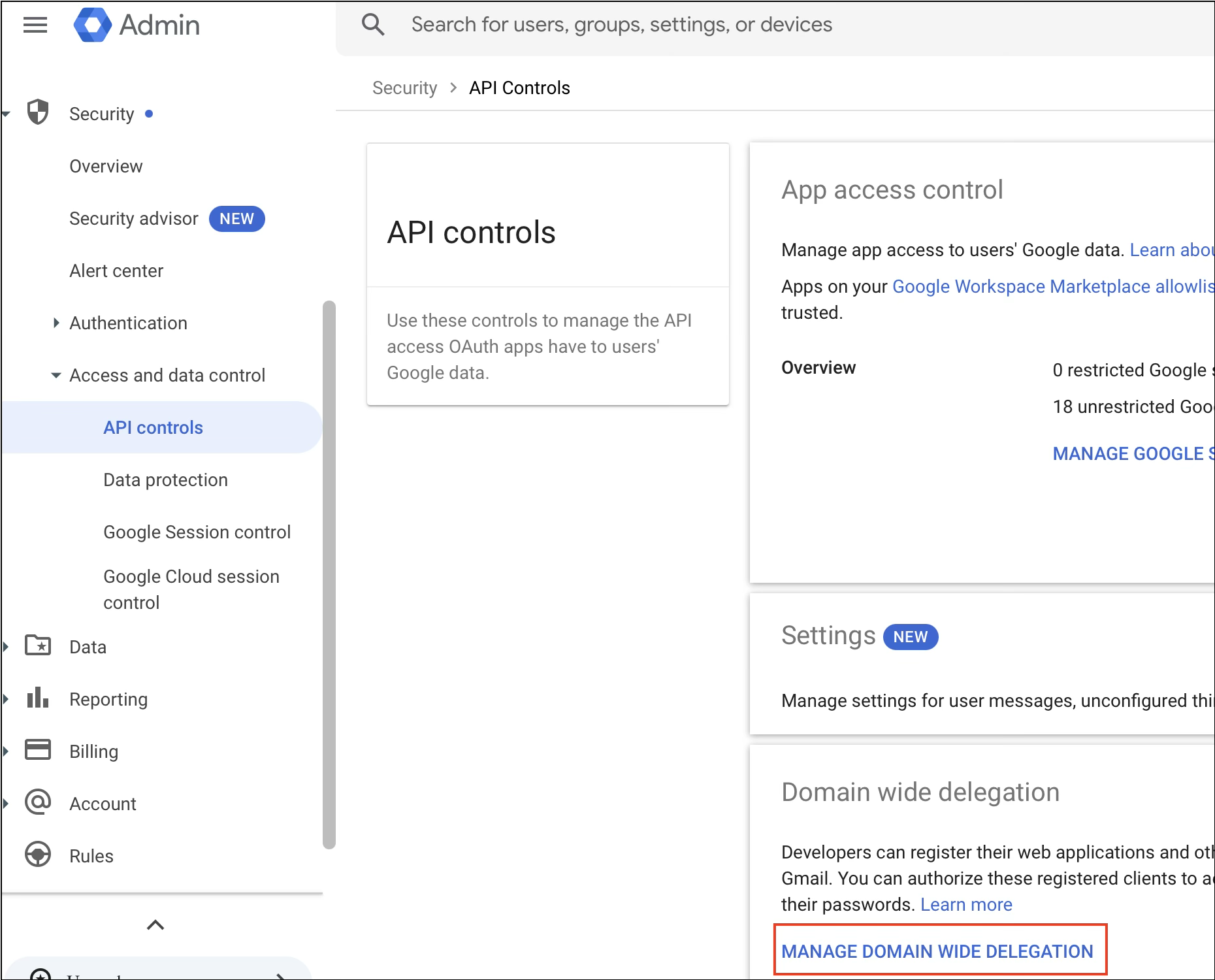
Step 4: Navigate to Domain-Wide Delegation Settings
In the Google Admin Console:
Go to Security.
Select Access and data control.
Click API controls.
Navigate to Domain-wide delegation.
Click Manage Domain-Wide Delegation.
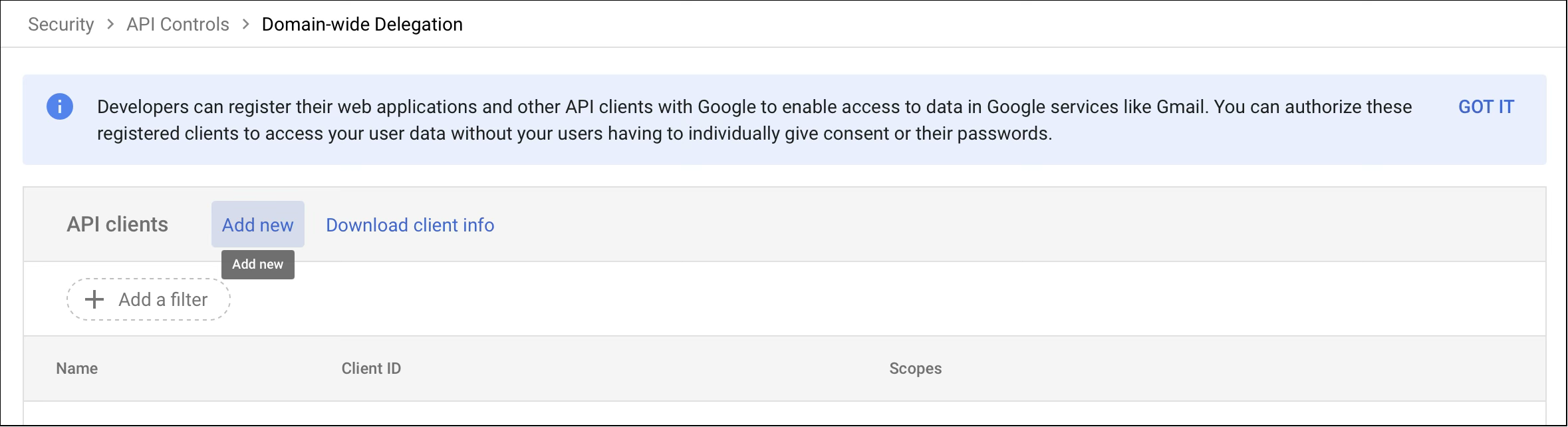
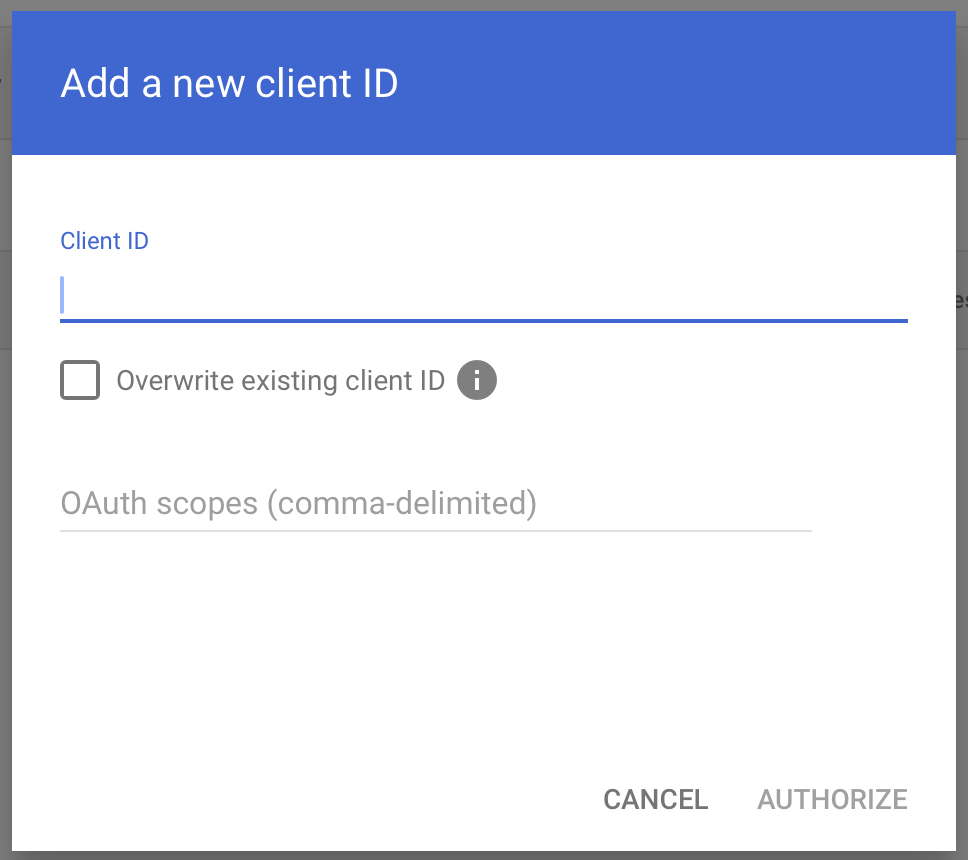
Step 5: Add a New Client ID
In the Domain-wide delegation page, click Add new.
The Add a new client ID dialog opens.
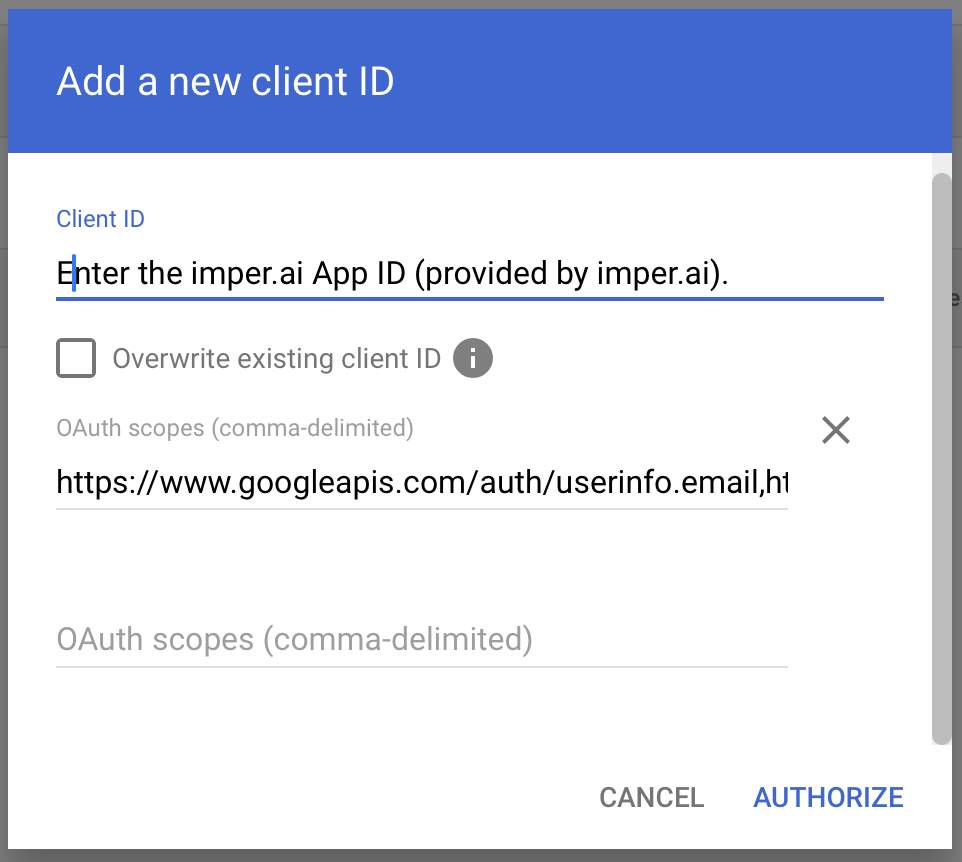
Step 6: Authorize imper.ai (Domain-Wide Delegation)
In the Client ID field, enter the imper.ai App (Client) ID provided during onboarding.
In the OAuth scopes field, paste the scopes you copied earlier from imper.ai.
Click Authorize (or Save, depending on your console version).
This completes the Domain-Wide Delegation configuration.
This is a one-time setup performed by a Google Workspace Super Admin.
It authorizes imper.ai to securely access approved Google APIs on behalf of users in your organization.
Permissions Granted
When connecting Google Workspace as an IdP, imper.ai requests access to specific Google APIs.
These Google Workspace permissions allow imper.ai to retrieve identity and organizational context required for verification and meeting protection.
Permissions Requested From All Monitored Users
googleapis.com/auth/userinfo.email
Description: View the user’s email address
Used for: Identifying the user and linking their Google account
googleapis.com/auth/userinfo.profile
Description: Access basic profile information (name, profile image)
Used for: User identification and improved verification experience
googleapis.com/auth/meetings.space.readonly
Description: Read-only access to Google Meet spaces
Used for: Monitoring active meetings and enabling protection
googleapis.com/auth/meetings.space.created
Description: Access to Meet spaces created by the user
Used for: Tracking newly created meetings
googleapis.com/auth/calendar.readonly
Description: Read-only access to calendar settings and events
Used for: Syncing meeting metadata
googleapis.com/auth/calendar.events
Description: Access to view, create, and modify calendar events
Used for: Creating or updating meetings so they can be monitored
Permissions Requested From Google Workspace Admin Only
googleapis.com/auth/admin.directory.user.readonly
Description: Read-only access to users in the organization
Used for: Reading directory users to enable monitoring
googleapis.com/auth/admin.reports.audit.readonly
Description: Read-only access to Google Workspace audit logs
Used for: Monitoring user activity, security events, and compliance
Additional temporary permissions may appear during deployment.
These can be manually removed after the integration is complete.
Integration Status
Once authorization is complete:
Google Workspace appears as Connected on the Integrations page in imper.ai
The integration becomes immediately available for Google Meet protection
No additional configuration is required at this stage.
What This Enables
After connecting Google Workspace and completing Domain-Wide Delegation, imper.ai can:
Distinguish internal vs. external participants
Associate meeting participants with organizational context
Improve detection of impersonation and social engineering attempts
This connection is a prerequisite for enabling Google Meet protection.
Next Steps: Complete Google Workspace Onboarding
After completing Domain-Wide Delegation:
Return to Admin Console > Integrations in imper.ai.
Complete the remaining onboarding steps, including: