imper.ai protects real-time communication channels (voice, video, chat) by verifying that every participant is truly who they claim to be. It eliminates impersonation attempts by combining multi-layer identity checks, AI-driven behavioural analysis, and continuous verification throughout the conversation.
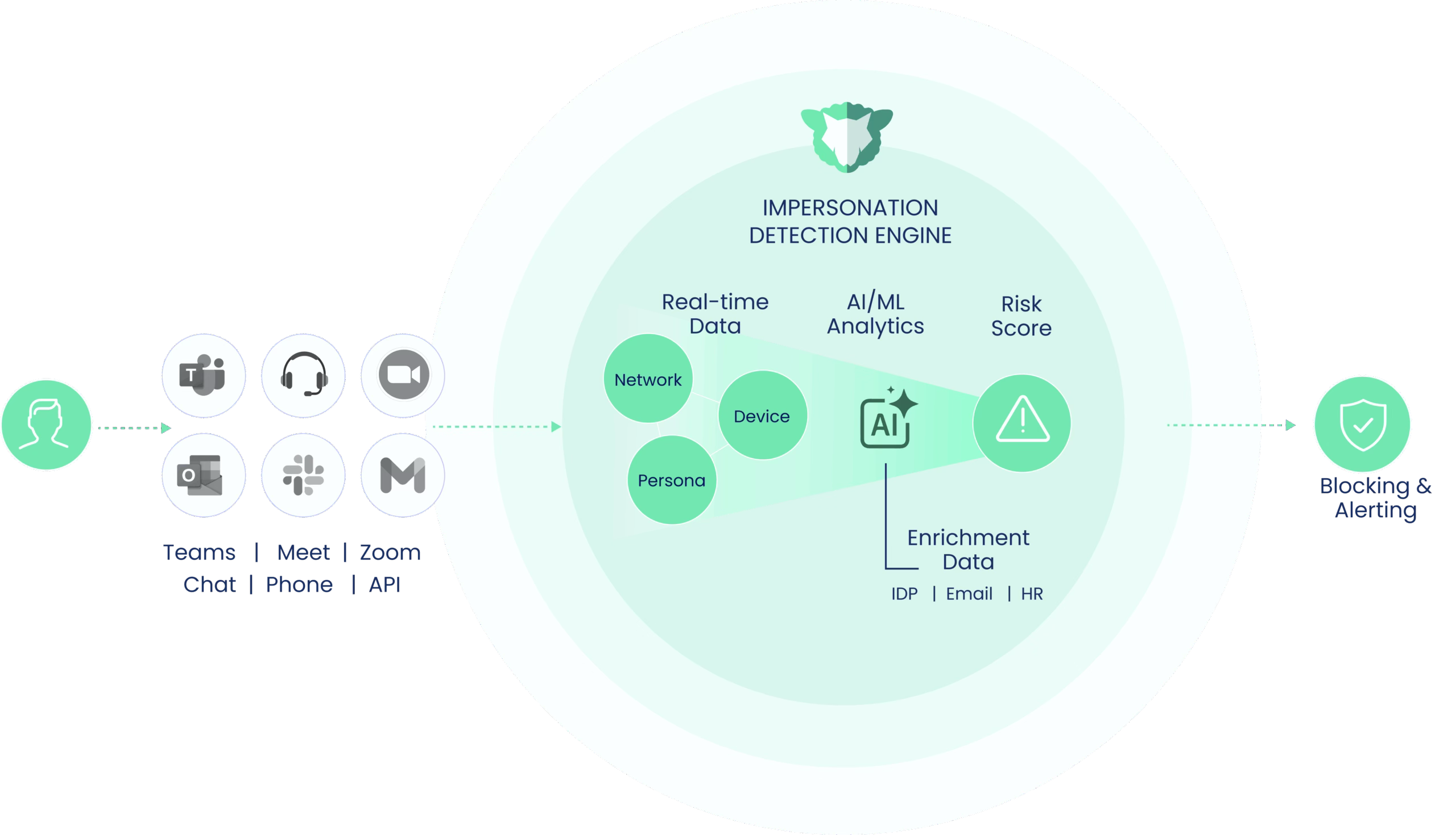
This article explains the core components of the Impera platform and how the verification process works end-to-end.
1. What imper.ai Does
imper.ai prevents impersonation attacks across calls, meetings, and collaboration tools by:
-
Verifying users before a conversation starts
-
Continuously validating identity signals during the call
-
Detecting anomalies, deepfake activity, or behavioural deviations
-
Alerting or blocking suspicious communication in real time
It acts as a security layer that wraps around your existing communication stack—Zoom, Teams, Google Meet, Slack, WhatsApp, phone calls, and more.
2. Core Platform Components
2.1 Verification Engine
A multi-stage verification engine that confirms the identity of every participant using:
-
Device characteristics
-
Network patterns
-
Voice, tone, and behaviour
-
Historical consistency
-
Organisation-level identity sources (Entra, Okta, Google Workspace, etc.)
The engine runs continuously, not only at login.
2.2 Conversation Guard
A real-time protection layer that monitors the live interaction and detects:
-
Deepfake voice injection
-
Pretexting and impersonation attempts
-
Abnormal language patterns
-
Impossible behaviour (e.g., “CEO calling from two places at once”)
-
Indicators of fraud or social engineering
If something looks wrong, imper.ai can warn the employee, block the session, or escalate to security.
2.3 Identity Graph
A constantly-updated map of your organisation’s users and communication patterns.
It learns “normal” behaviour for individuals and teams, improving detection accuracy.
Feeds include:
-
Directory services (Azure AD, Okta, Google)
-
Communication metadata
-
Device fingerprints
-
Historical verification data
2.4 Secure Communication Integrations
imper.ai connects to your organisation’s communication tools to enforce identity assurance wherever conversations happen:
-
Collaboration: Teams, Slack, Google Workspace
-
Meetings: Zoom, Google Meet, Teams
-
Voice Calls: SIP, Twilio, PBX, mobile numbers
-
Messaging: SMS, WhatsApp, chat channels
Integration requires minimal setup—typically OAuth or admin-level app installation.
3. How imper.ai Works (End-to-End Flow)
Step 1: User Attempts to Join a Call or Conversation
A user initiates or joins a meeting, phone call, or chat.
imper.ai intercepts the request and checks:
-
Who is this user?
-
Is this user expected to join?
-
Is their device/network consistent?
Step 2: Identity Verification
imper.ai runs layered identity checks:
-
Directory Identity – Cross-checked with your IdP
-
Device Identity – Fingerprinting, environment checks
-
Behavioural Identity – Typing rhythm, voice tempo, typical login times
-
Risk Scoring – If something is off, Impera escalates verification (MFA, code, callback, etc.)
Verification is silent to the user unless risk is detected.
Step 3: Session Protection (Live Call Monitoring)
Once the meeting or call begins, Impera monitors in real time:
-
Voice for deepfake markers
-
Language for pretexting red flags
-
Behaviour for unusual requests (“urgent transfer”, “reset password”, “share access link”)
-
Participant profiles for anomalies
Suspicious activity triggers:
-
User notification
-
On-screen banners
-
Call termination (optional)
-
SOC alerts
Step 4: Post-Call Intelligence
After the interaction ends, Impera records:
-
Verification results
-
Risk level
-
Any alerts triggered
-
Identity anomaly trends
-
Recommendations for security
These insights appear in the imper.ai admin console.